How Cisco ISE and TrustSec Work Together for Network Security
Cisco ISE and TrustSec: Network Security Strategies
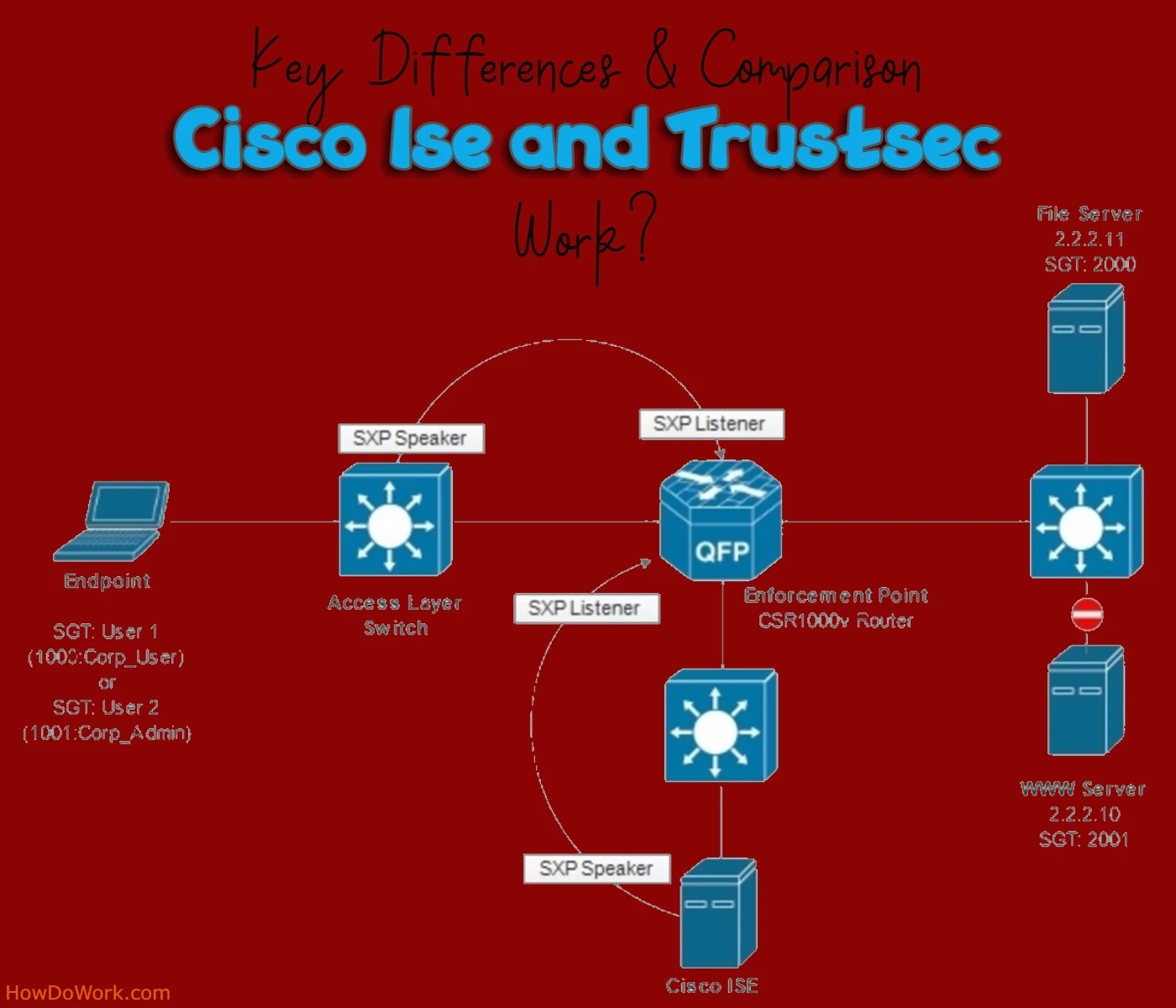
Cisco ISE and TrustSec are crucial elements in network security. Cisco Identity Services Engine (ISE) primarily focuses on controlling who can access a network by verifying user and device identities, enforcing authorization policies, and even conducting posture assessments. In contrast, Cisco TrustSec is geared towards securing data within the network by classifying data, implementing role-based access controls, and encrypting sensitive information. While ISE ensures network access security, TrustSec safeguards data integrity, and together, they create a formidable defense against cyber threats within your network.
| Aspect | Cisco ISE | Cisco TrustSec |
|---|---|---|
| Primary Focus | Network Access Control (NAC) | Data Security and Access Control |
| Functionality | Controls who can access the network | Controls who can access specific data |
| Authentication | User and device authentication | Data classification and role-based access |
| Authorization | Determines network access privileges | Dictates access to specific data |
| Posture Assessment | Ensures device compliance with security | N/A |
| Guest Access | Provides controlled access for guests | N/A |
| Data Encryption | Focuses on network access control | Provides data-level encryption |
| Integration | Integrates with various security solutions | Focused on data-centric security |
| Network Segmentation | Can enforce network segmentation | Enforces segmentation based on data |
Contents
Understanding Cisco ISE
Cisco ISE (Identity Services Engine) is a comprehensive network access control (NAC) solution that provides secure access to your network while enforcing policies to ensure compliance and security. Its primary goal is to authenticate and authorize users and devices, ensuring that they meet specific security criteria before granting access to network resources.
How Cisco ISE Works
Cisco ISE operates by employing a combination of technologies and processes to secure your network. Here’s a brief overview of how it works:
- Authentication: Cisco ISE verifies the identity of users and devices trying to connect to the network. It can use a variety of authentication methods, including 802.1X, MAB (MAC Address Bypass), and web-based authentication.
- Authorization: After successful authentication, ISE determines what level of access should be granted to the user or device based on predefined policies. Access policies can be highly granular, allowing you to specify which network resources each user or device can access.
- Posture Assessment: ISE can perform endpoint posture assessments to ensure that devices meet security compliance standards. For example, it can check if a device has the latest antivirus updates before granting access.
- Guest Access: Cisco ISE can provide guest access to users who do not have corporate credentials, ensuring that they have restricted and controlled access to the network.
- Integration with Other Security Solutions: ISE can integrate with other security solutions like firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) to provide an additional layer of security.
Understanding Cisco TrustSec
Cisco TrustSec, on the other hand, is a technology that focuses on securing data within the network by implementing role-based access controls (RBAC). While Cisco ISE mainly deals with controlling who can access the network, TrustSec’s primary objective is to control who can access specific data within the network.
How Cisco TrustSec Works
Let’s dive into the workings of Cisco TrustSec:
- Classification: TrustSec classifies data based on its sensitivity. This classification can be manual or automatic, depending on the policies you define.
- Role-Based Access Control (RBAC): TrustSec assigns roles to users or devices based on their identity and the classified data they are trying to access. These roles dictate what actions can be performed on the data.
- Encryption: TrustSec can encrypt data flows between devices to ensure that sensitive information remains confidential, even within the network.
- Segmentation: TrustSec enforces network segmentation to separate different data classifications, preventing unauthorized access to sensitive information.
Now that we have a basic understanding of Cisco ISE and TrustSec, let’s compare them in terms of key differences.
Key Differences between Cisco ISE and TrustSec
When it comes to Cisco ISE and TrustSec, there are several key differences that set them apart in terms of their focus and functionality. Here’s a breakdown of these differences:
| Aspect | Cisco ISE | Cisco TrustSec |
|---|---|---|
| Primary Focus | Network Access Control (NAC) | Data Security and Access Control |
| Functionality | Controls who can access the network | Controls who can access specific data |
| Authentication | User and device authentication | Data classification and role-based access |
| Authorization | Determines network access privileges | Dictates access to specific data |
| Posture Assessment | Ensures device compliance with security | N/A |
| Guest Access | Provides controlled access for guests | N/A |
| Data Encryption | Focuses on network access control | Provides data-level encryption |
| Integration | Integrates with various security solutions | Focused on data-centric security |
| Network Segmentation | Can enforce network segmentation | Enforces segmentation based on data |
Cisco ISE vs. TrustSec: When to Use Which
The choice between Cisco ISE and TrustSec depends on your organization’s specific security needs and objectives. Let’s explore some scenarios where one may be more suitable than the other:
- Use Cisco ISE When…
- You need to control who can access your network resources.
- You want to enforce authentication and authorization policies for users and devices.
- Posture assessment and guest access control are crucial requirements.
- You require integration with other security solutions to enhance network security.
- Use Cisco TrustSec When…
- You want to protect sensitive data within your network.
- Data classification and role-based access control are top priorities.
- You need to ensure that data remains confidential through encryption.
- Network segmentation based on data sensitivity is a key requirement.
The Synergy Between Cisco ISE and TrustSec
While Cisco ISE and TrustSec serve different primary purposes, they can complement each other to create a robust security ecosystem within your network. Here’s how they can work together:
- Enhanced Access Control: By integrating Cisco ISE and TrustSec, you can ensure that not only are users and devices authorized to access the network, but they also have the appropriate permissions to access specific data. This dual-layer approach enhances security.
- Data Protection: Cisco ISE can enforce policies that restrict access to sensitive data, while TrustSec ensures that even within the network, data remains encrypted and accessible only to authorized users.
- Segmentation: The combination of network segmentation through Cisco ISE and data segmentation through TrustSec provides a comprehensive security framework that limits the scope of potential breaches.
- Compliance: Cisco ISE can verify the compliance of devices before granting network access, while TrustSec can ensure that data is accessed only by users or devices with the necessary permissions, aiding in regulatory compliance.
Conclusion
In the realm of network security, Cisco ISE and TrustSec are two indispensable tools with distinct yet complementary roles. Cisco ISE focuses on controlling who can access your network and enforcing policies at the network level, while TrustSec takes data-centric security to the next level by classifying data, implementing role-based access controls, and encrypting sensitive information.
When deciding between Cisco ISE and TrustSec, it’s essential to assess your organization’s specific security needs. In many cases, these two technologies can work in tandem to provide comprehensive protection for your network and data. By understanding the key differences and their respective strengths, you can make informed decisions to fortify your network security strategy.
FAQs
Cisco ISE, or Identity Services Engine, is a network access control (NAC) solution. It works by authenticating and authorizing users and devices attempting to access a network. ISE enforces security policies, conducts posture assessments, and can even provide controlled guest access. It integrates with various authentication methods and security solutions to ensure secure network access.
Cisco TrustSec focuses on data-centric security within a network. It classifies data based on its sensitivity, assigns role-based access controls (RBAC) to users and devices, and encrypts data flows to protect sensitive information. Its primary function is to control who can access specific data and ensure data confidentiality.
Cisco ISE and TrustSec work together to enhance network security. ISE controls network access, ensuring that only authorized users and devices can connect. TrustSec, on the other hand, secures data within the network. By integrating the two, you establish a multi-layered security framework that safeguards both network access and data integrity.
Cisco ISE supports various authentication methods, including 802.1X, MAC Address Bypass (MAB), and web-based authentication. These methods help verify the identity of users and devices before granting access to the network.
TrustSec classifies data based on its sensitivity. This classification can be manual or automatic, depending on the policies you define. It allows you to identify which data is more critical and requires stricter access controls.
Yes, TrustSec can encrypt data flows between devices to ensure that sensitive information remains confidential. This encryption adds an extra layer of security to protect data as it moves within the network.
Yes, Cisco ISE can integrate with various security solutions such as firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS). This integration enhances overall network security by coordinating with other security measures.
Cisco ISE can verify device compliance before granting network access, while TrustSec ensures that data is accessed only by authorized users or devices. This collaborative approach aids in achieving and maintaining regulatory compliance.
You should consider using Cisco ISE when you need to control who can access your network, enforce authentication and authorization policies, manage guest access, and integrate with other security solutions to bolster network security.
Cisco TrustSec is an excellent choice when you want to focus on securing data within your network, implement data classification and role-based access controls, encrypt sensitive data, and enforce network segmentation based on data sensitivity.